ANGRYPOUTINE
题目
## SCENARIO
LAN segment data:
- LAN segment range: 10.9.10.0/24 (10.9.10.0 through 10.9.10.255)
- Domain: angrypoutine.com
- Domain controller: 10.9.10.9 - ANGRYPOUTINE-DC
- LAN segment gateway: 10.9.10.1
- LAN segment broadcast address: 10.9.10.255
## TASK
Write an incident report based on the pcap and the alerts.
The incident report should contains 3 sections:
- Executive Summary: State in simple, direct terms what happened (when, who, what).
- Details: Details of the victim (hostname, IP address, MAC address, Windows user account name).
- Indicators of Compromise (IOCs): IP addresses, domains and URLs associated with the infection. SHA256 hashes if any malware binaries can be extracted from the pcap.
调查过程
根据题目中的要求,本次的任务目标为:
- 攻击总结:何时、谁、做了什么
- 受害者信息:Hostname、IP地址、MAC地址、Windows用户名
- IOCs(失陷指标):与感染相关的IP地址、域名、URL等,恶意软件的SHA256(如果流量包中存在)
基本情况排查
资产排查
首先排查自身资产:
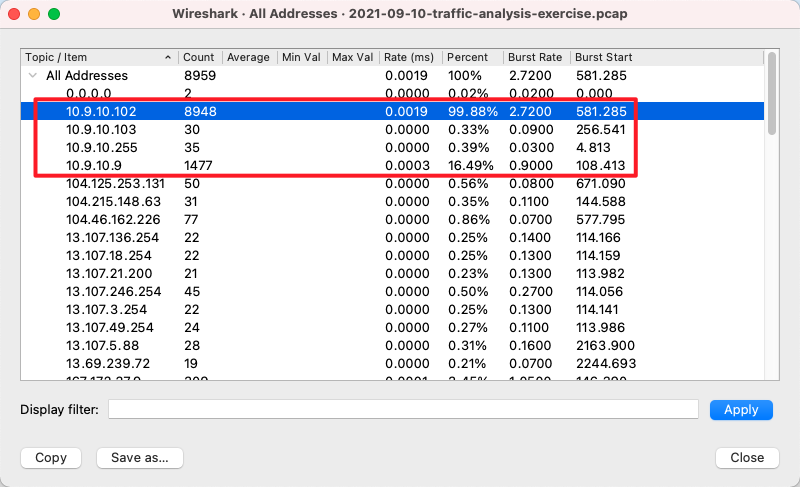
图:IPv4统计信息
按照通讯数量占比排序,内网主机有:
- 10.9.10.102
- 10.9.10.9
- 10.9.10.255
- 10.9.10.103
通讯协议排查
通过统计IPv4地址间通讯占比,发现比例相对正常:

图:IPv4通信协议占比
载荷排查
选择导出HTTP对象,根据文件大小排序:
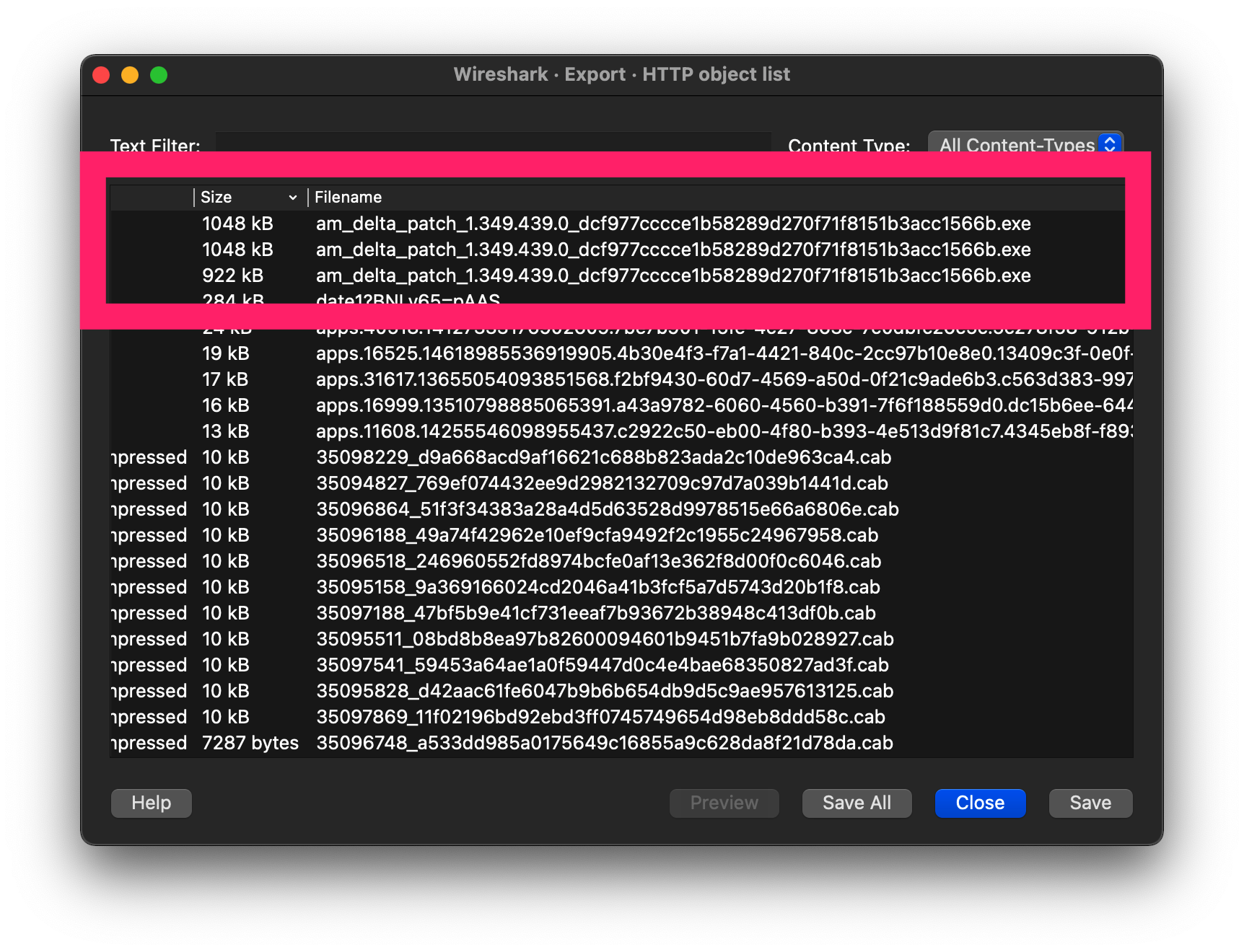
图:HTTP对象导出
发现文件较大的头部三个PE文件比较可疑:
am_delta_patch_1.349.439.0_dcf977cccce1b58289d270f71f8151b3acc1566b(1).exe
am_delta_patch_1.349.439.0_dcf977cccce1b58289d270f71f8151b3acc1566b(2).exe
am_delta_patch_1.349.439.0_dcf977cccce1b58289d270f71f8151b3acc1566b(3).exe
am_delta_patch_1.349.439.0_dcf977cccce1b58289d270f71f8151b3acc1566b(4).exe
am_delta_patch_1.349.439.0_dcf977cccce1b58289d270f71f8151b3acc1566b.exe
但上传VT后均没有报毒,且通讯的Host为:au.download.windowsupdate.com,在微软官网上查询到是合法地址:
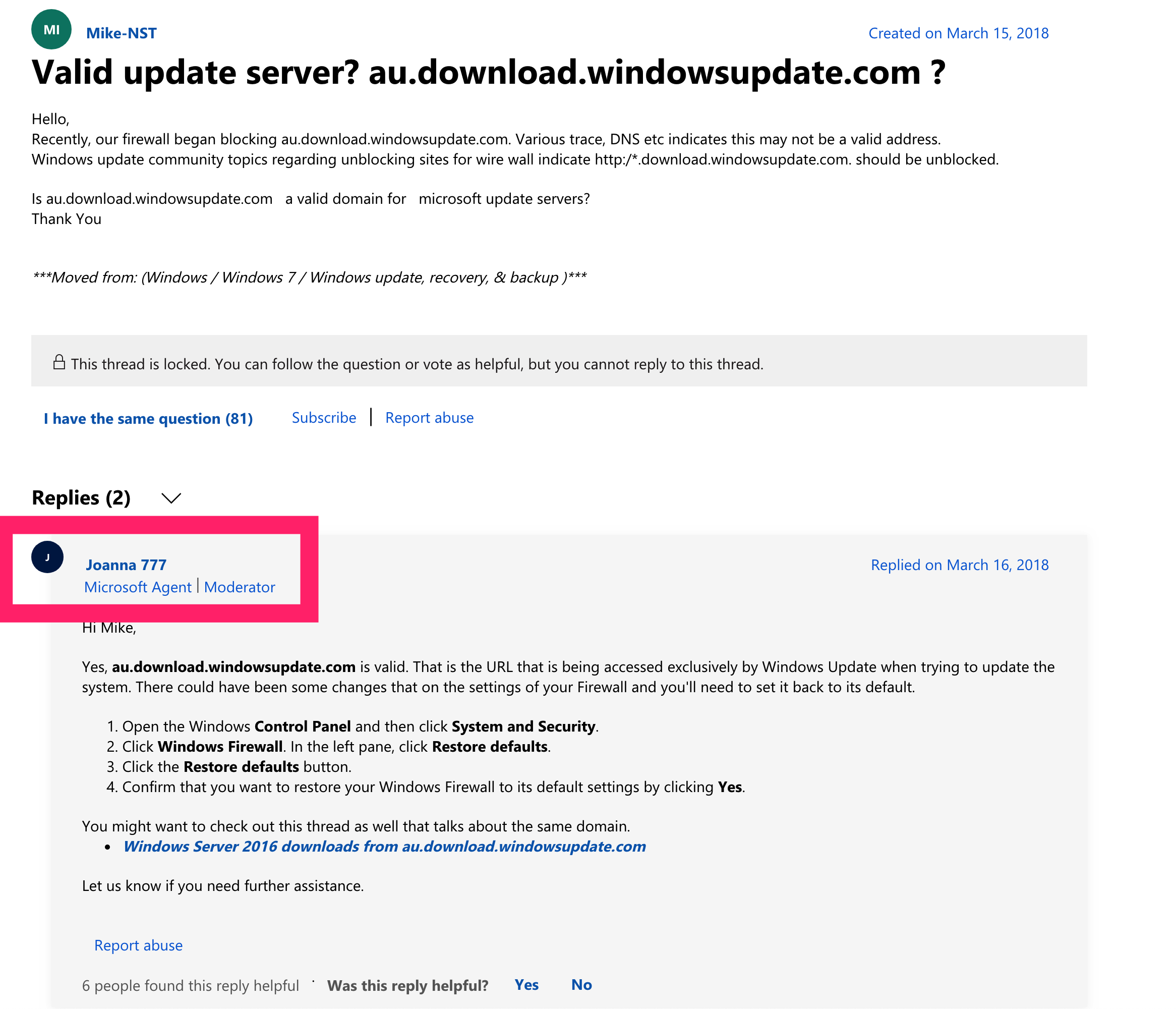
图:微软社区问答
暂时排除上述域名的嫌疑后,发现一个具有相对异常请求参数的通讯文件,date、pAAS,疑似时间与密码,嫌疑较大:
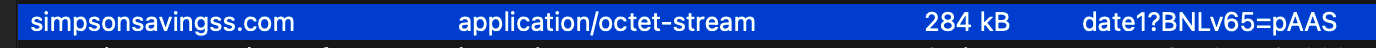
图:具有异常请求参数的文件
导出对应文件,VT查杀报毒:
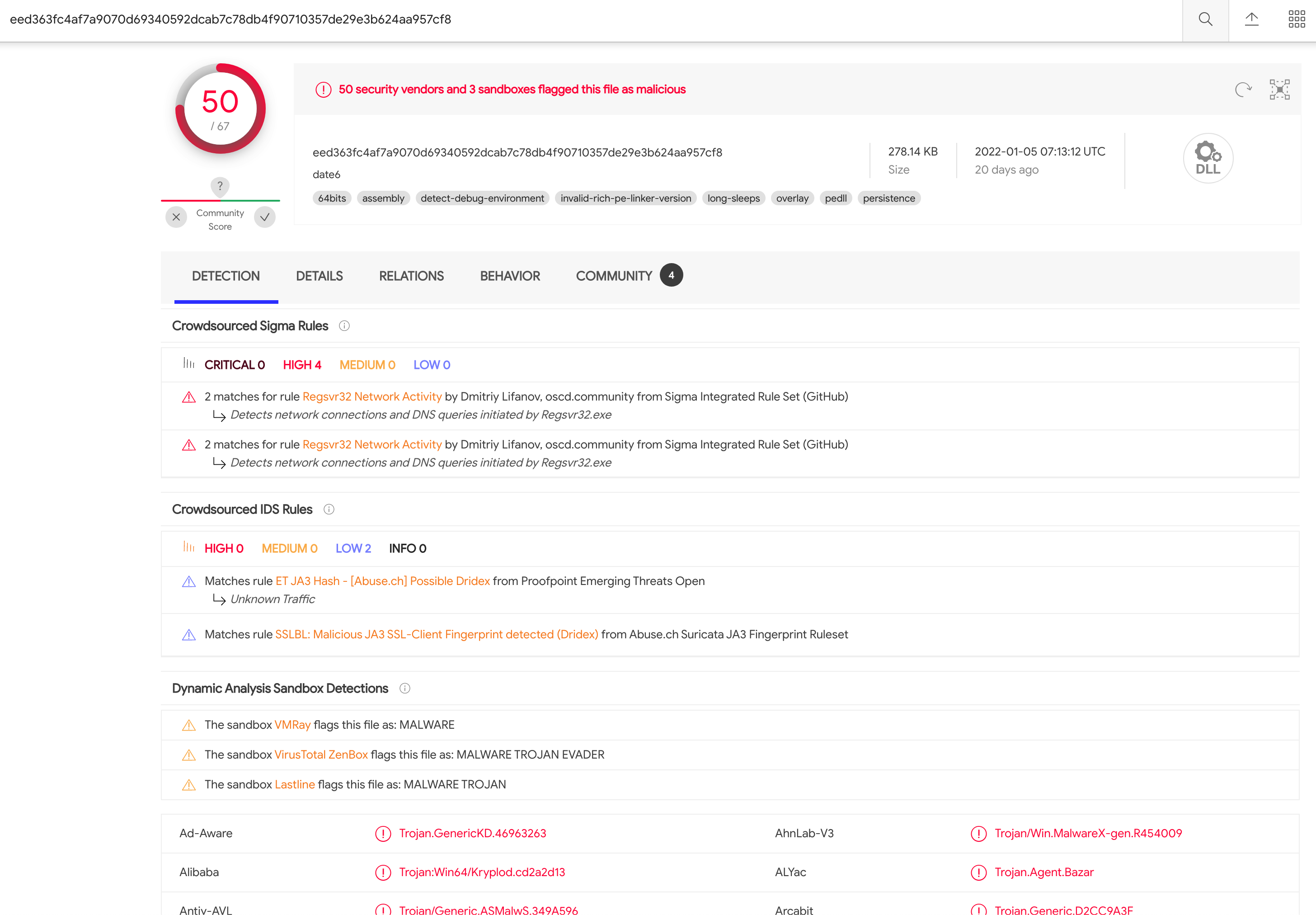
图:异常请求参数文件的VT查杀情况
记录文件哈希为:eed363fc4af7a9070d69340592dcab7c78db4f90710357de29e3b624aa957cf8,外部IP地址为:194.62.42.206,内部IP为:10.9.10.102。
感染路径排查
发现报毒文件后,定位到该文件的通讯包序号为:1475,定位到请求的URI为:http://simpsonsavingss.com/bmdff/BhoHsCtZ/MLdmpfjaX/5uFG3Dz7yt/date1?BNLv65=pAAS。接下来开始排查感染路径。
定位外部IP
首先,检索恶意外部IP,定位最早与之交互的内网IP,以及交互的协议类型,这是为了弄清楚攻击者“怎么进来的?”:
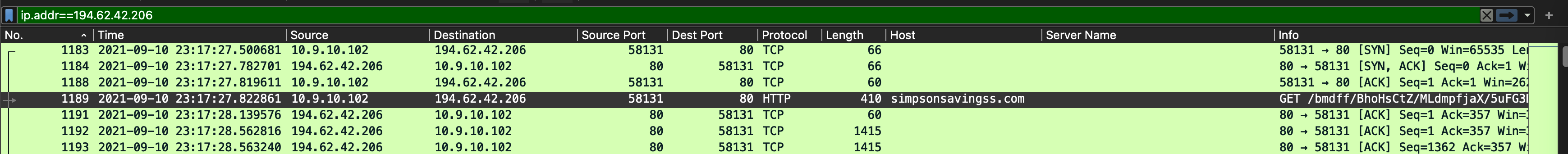
图:恶意IP交互
可以发现,该恶意IP最早交互的IP即为10.9.10.102,第一次交互情况就是开始从下载远控木马。
定位内部IP
接下来需要定位最早交互/失陷主机,通过排查该主机的通讯情况,来弄清楚受害者”做了什么?“:
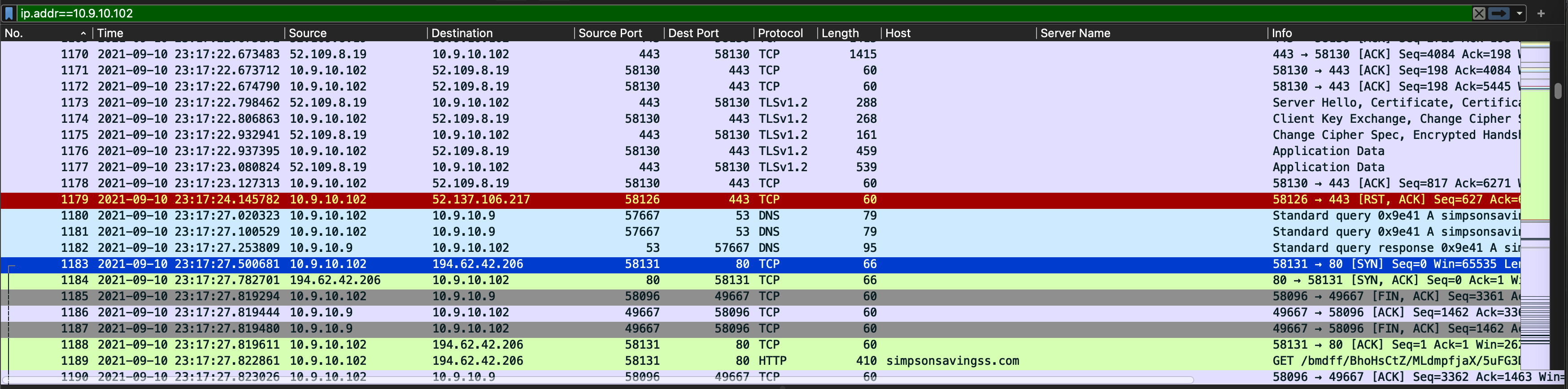
图:内部主机通讯情况排查
通过初步排查,该主机在与恶意IP交互前(Packet No. 1184),似乎是正常在使用Windows服务,暂时没有发现该主机主动访问异常网站服务的通讯。可以尝试排查是否有邮件服务的相关通讯,因为点击钓鱼邮件中的恶意链接是投递情况。
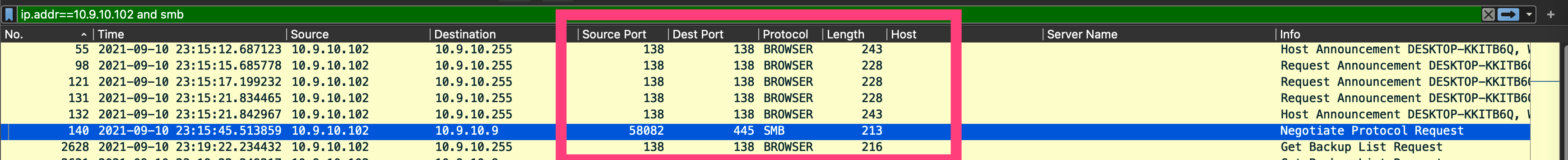
图:排查邮件服务的通讯情况
通过过滤smb协议和受害主机IP,我们发现,在受害主机访问载荷投递链接之前,邮件通讯协议是“Browser”(作为域控+邮件服务器的IP:10.9.10.9需要先查找到网络中的主机)。SMB协议通讯的信息中显示为”Negotiate Protocol Request“,即在协商协议请求。因此初步判断是存在邮件发送到受害主机的情况。
横向移动排查
通过排查受害主机IP和域控IP与内网中其他主机的交互,来排查横向移动的情况。
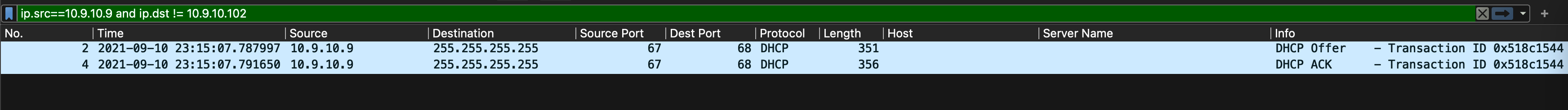
图:域控IP与其他主机交互情况
ip.src==10.9.10.102 and ip.dst != 10.9.10.9 and ip.dst ==10.9.10.0/24
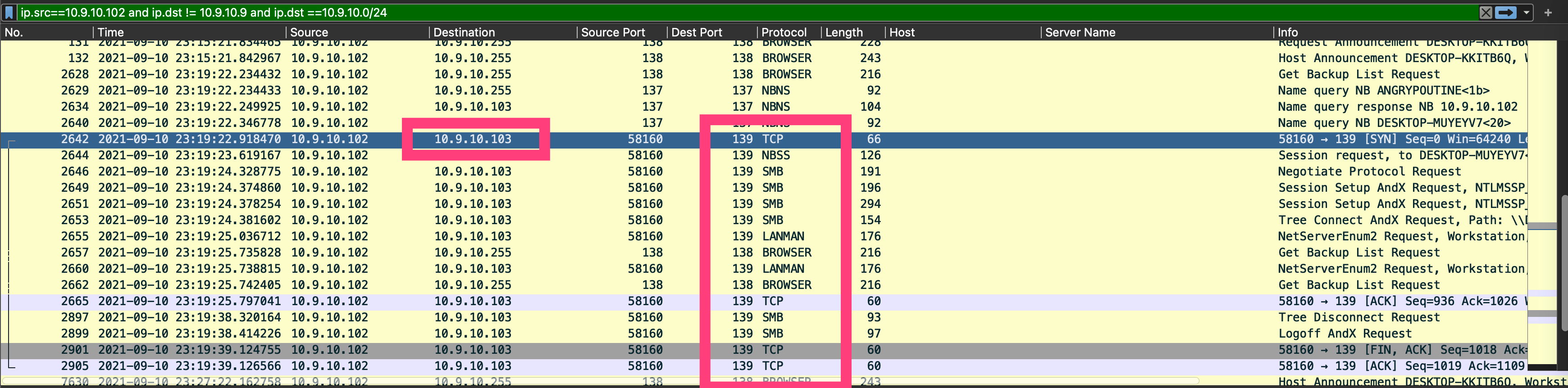
图:受害主机与内网其他主机交互情况
可以发现,受害主机在感染后,与内网主机10.9.10.103进行通讯,且通讯协议依次为:
TCP
NBSS
SMB
LANMAN
BROWSER
TCP
SMB
......
这是较为明显的发送邮件行为,因此也怀疑10.9.10.103被攻击。
结果
攻击总结
受害者信息
通过NBNS通讯,可以找到受害主机MAC地址:
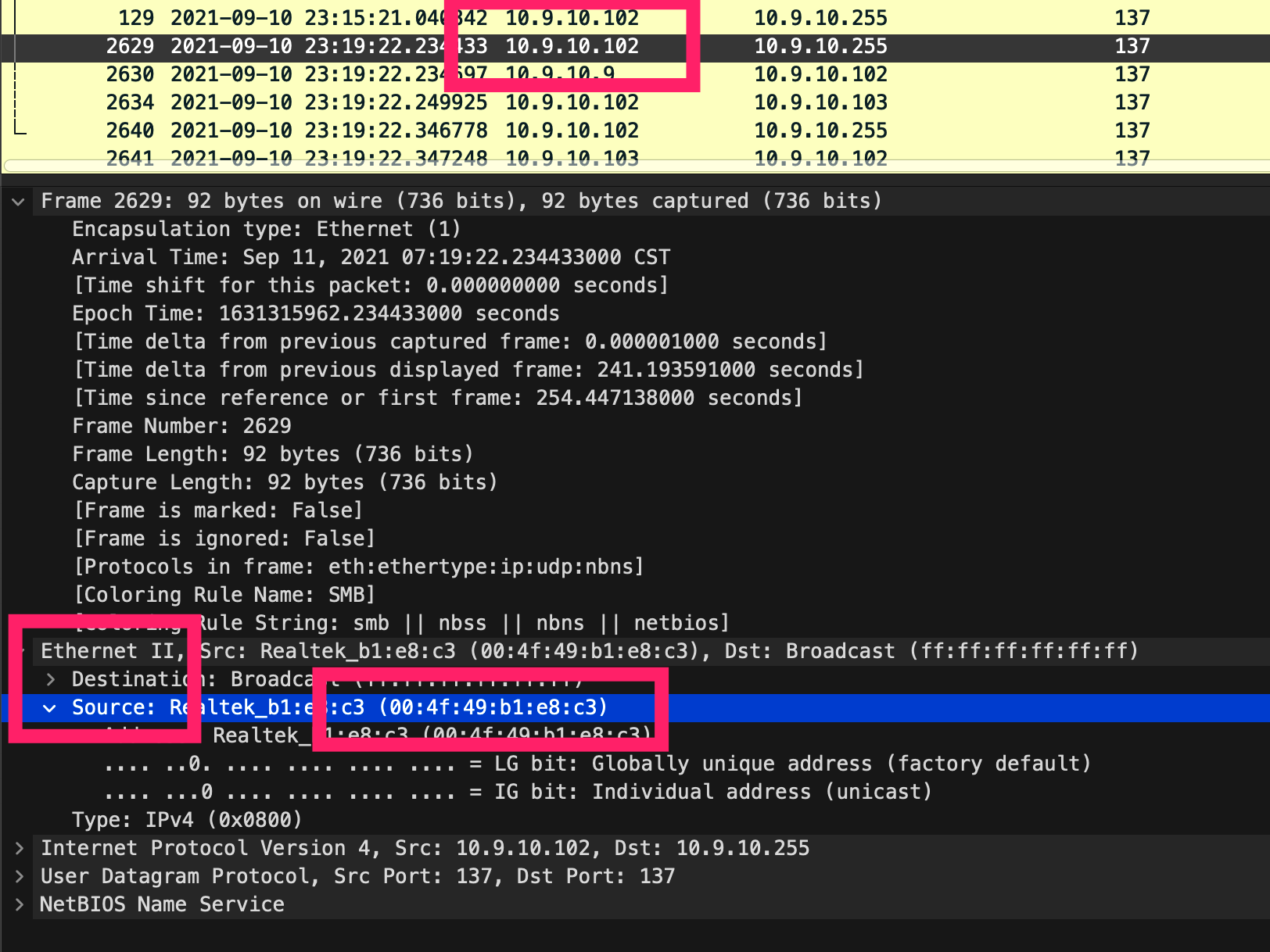 图:定位受害主机MAC地址
图:定位受害主机MAC地址
同样,在NBNS通讯中,也可以定位受害主机的Hostname:
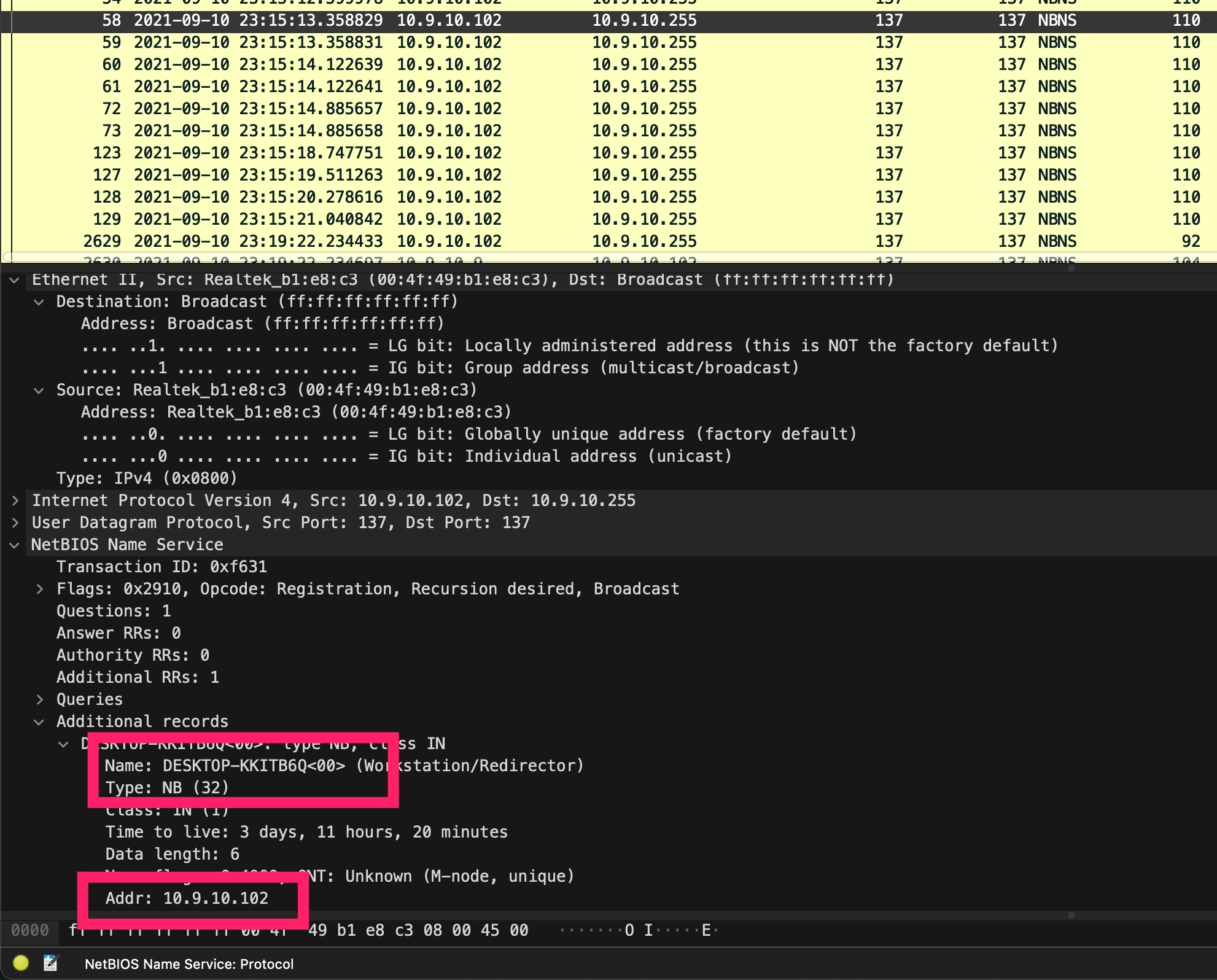
图:定位受害主机的Hostname
通过Kerberos通讯(前提是需要在Active Directory (AD) 环境中的 Windows 主机),可以发现Windows账户名:
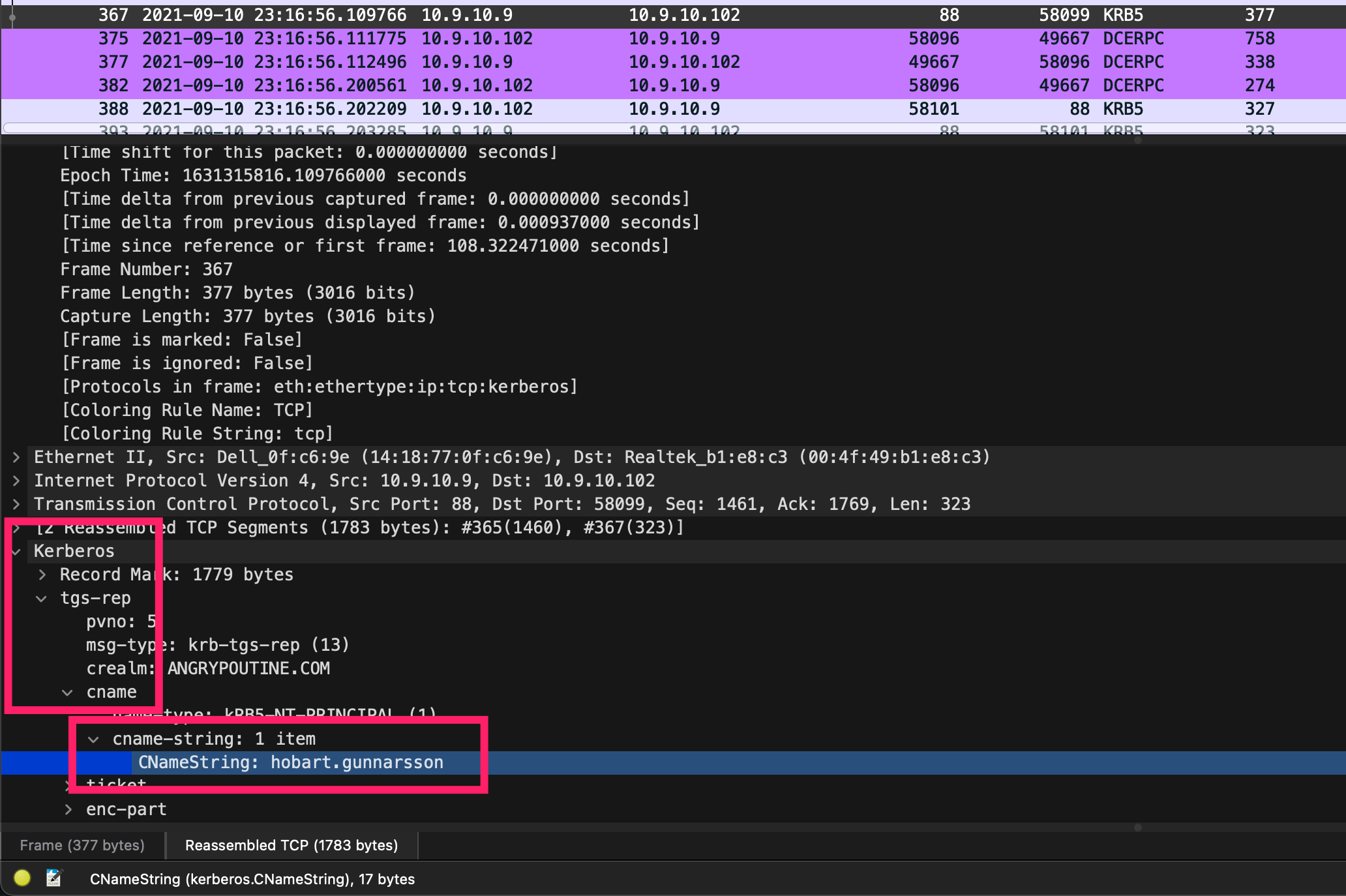
图:定位受害主机Windows用户名
| IP | MAC | Hostname | Windows user account name |
|---|---|---|---|
| 10.9.10.102 | 00:4f:49:b1:e8:c3 | DESKTOP-KKITB6Q<00> (Workstation/Redirector) | hobart.gunnarsson |
IOCs
Domain
simpsonsavingss[.]com
IP
194[.]62[.]42[.]206
SHA256
eed363fc4af7a9070d69340592dcab7c78db4f90710357de29e3b624aa957cf8
标准答案
Indicators of Compromise (IOCs)
Traffic to retrieve BazarLoader DLL:
• 194.62.42.206 port 80 - simpsonsavingss.com - GET /bmdff/BhoHsCtZ/MLdmpfjaX/5uFG3Dz7yt/date1?BNLv65=pAAS
Bazar C2 traffic:
- 167.172.37.9 port 443 - HTTPS traffic
- 94.158.245.52 port 443 - HTTPS traffic
NOTES:
The URL with /bmdff/ in the GET request returned a 64-bit DLL for BazarLoader. This /bmdff/ pattern has been used for the previous several weeks by the TA551 (Shathak) campaign.
SHA256 hash: eed363fc4af7a9070d69340592dcab7c78db4f90710357de29e3b6 24aa957cf8
-
File size: 284,816 bytes
-
File description: BazarLoader DLL
-
Tria.ge analysis: https://tria.ge/211004-vc7nsaggej
This DLL file is Windows-based malware, and it will infect a Windows computer if given the chance. I strongly recommend you do these procedures in a non- Windows environment.
Here's sandbox analysis of an email with a password-protected zip archive containing a Word doc on any.run. That Word doc generated an HTTP GET request to the same domain simpsonsavingss.com as seen in our exercise pcap.
• https://app.any.run/tasks/66e29996-8ad2-4d3e-b6a2-c74306b5ef3b/ This email also fits patterns of TA551 (Shathak) activity.
No follow-up Cobalt Strike or DarkVNC as we sometimes see with TA551 BazarLoader.
注意到,自己的答案中缺少了恶意主机IP端口的信息,并且缺少了Bazar C2的识别。BazarLoader DLL作为投递载荷只是第一步,后续建立C2通讯还可能会用到C2专用主机,后续需要注意!